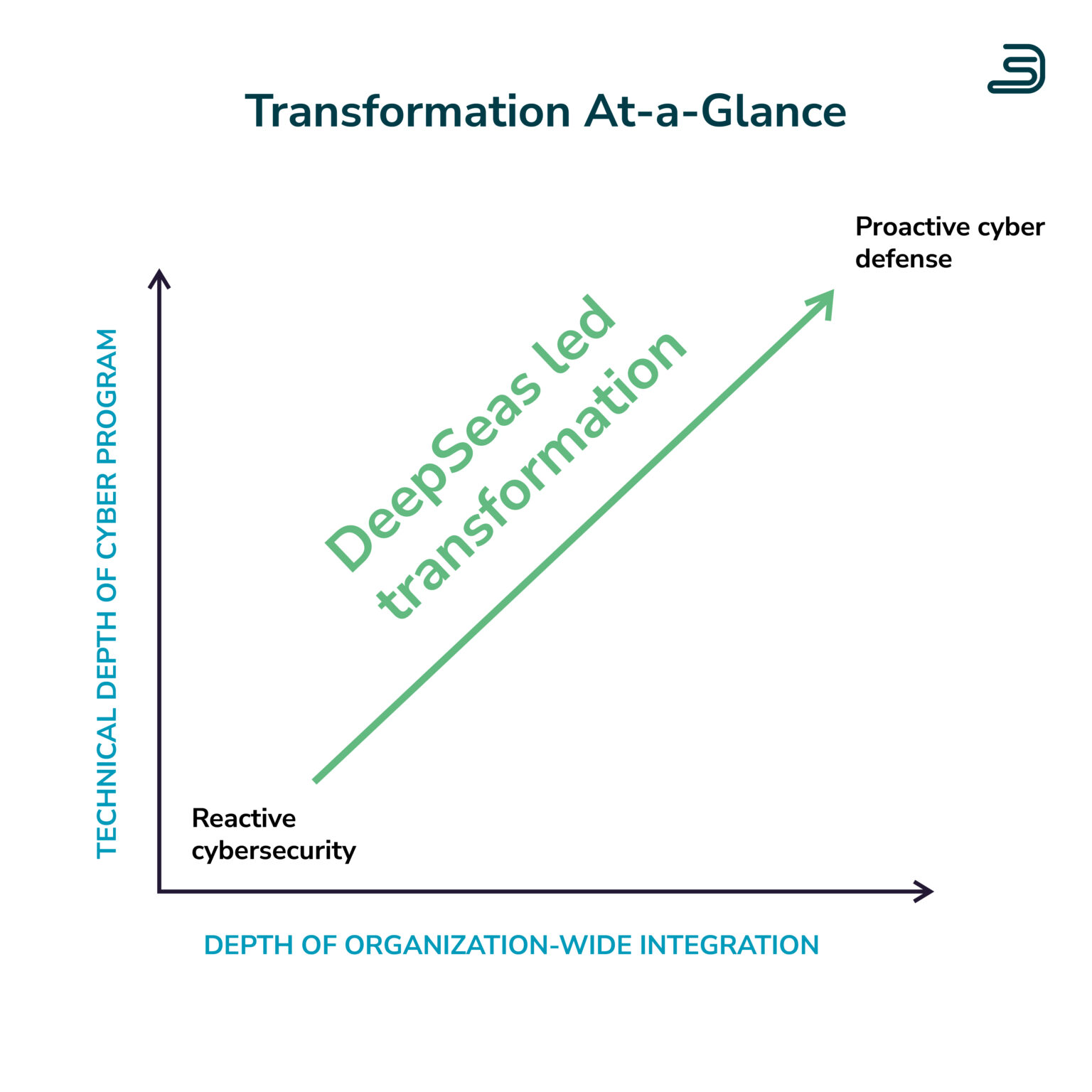
When you're ready to transform your cybersecurity program, it's OK to get help.
Craig Robinson, Research Vice President, IDC Security Services
Fuel your cyber transformation program with our flexible offerings.
Why DeepSeas?
DeepSeas is disrupting the Managed Detection & Response market with a differentiated experience for clients.
Ready to transform?
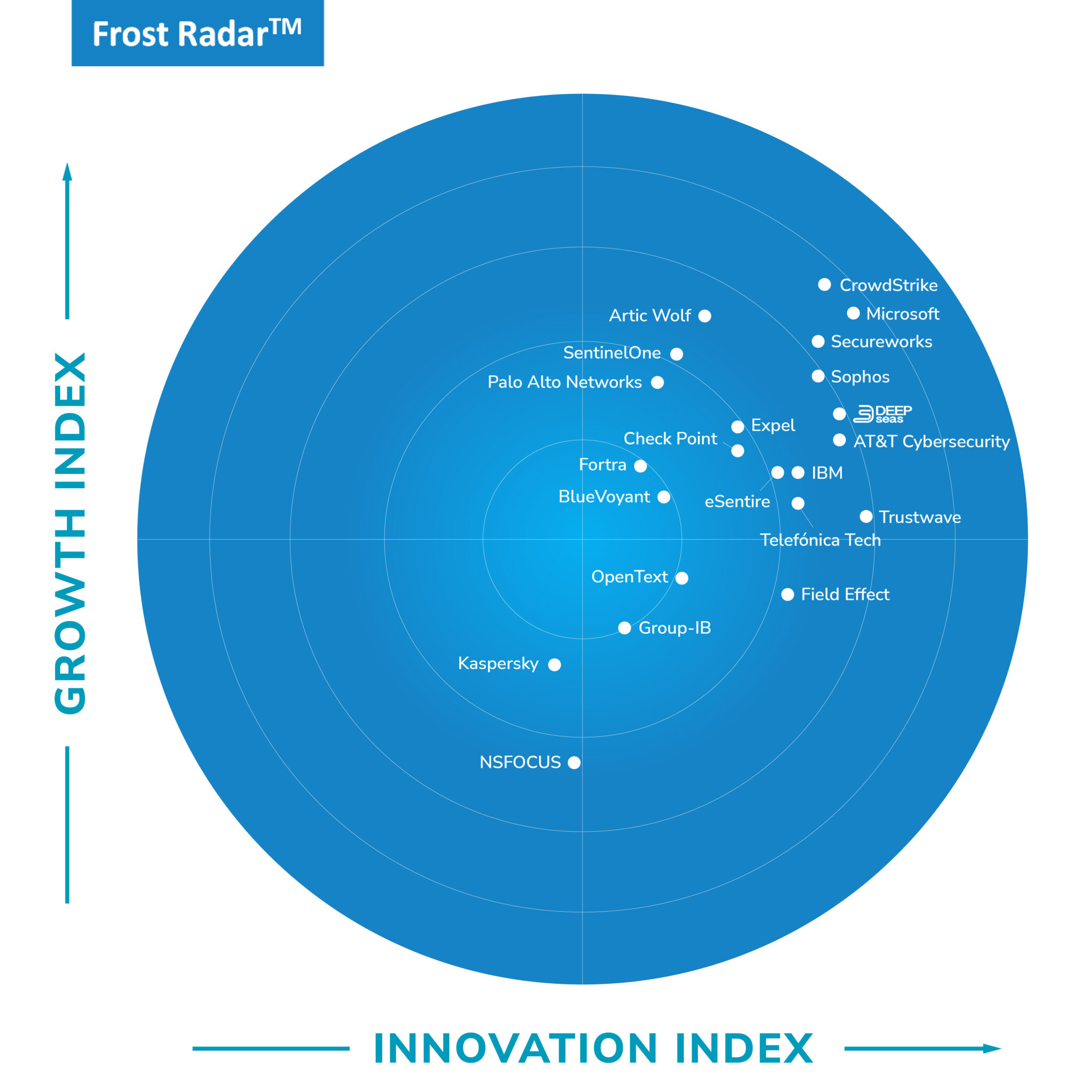
THE PROOF IS IN OUR PLATFORM.
Client Success Stories
There's one thing all
0
of our clients have in common:
They're transforming cybersecurity programs.

Financial Institution Facing Cyber Attacks Turns to DeepSeas for Persistent Defense
Learn more about how a finance organization facing escalating cyber attacks turned to DeepSeas for a robust, multi-layered defense strategy.

Life Sciences Company in M&A Process Leverages Compromise Assessment Service from DeepSeas
Learn more about how a client in the life sciences industry relied upon DeepSeas during a significant merger and acquisition process.

Healthcare Company Fills Leadership Gap with DeepSeas CISO Advisory
Learn more about how a healthcare provider turned to DeepSeas CISO Advisory to resolve a significant cybersecurity leadership gap.

Multinational Pharma Company Chooses DeepSeas for Vulnerability Management & Attack Surface Reduction
DeepSeas transforms cybersecurity for a pharmaceutical giant, boosting visibility, collaboration, and defense with formalized assessments and integration of threat intelligence.

Red Teaming Simulates Cyber Attack for Healthcare Organization
DeepSeas RED transforms healthcare cybersecurity, simulating real-world attacks to validate defenses, enhance processes, and ensure compliance with industry standards like NIST 800-53 and HIPAA.

Manufacturer Chooses DeepSeas OT Cybersecurity Services
DeepSeas revolutionizes manufacturing cybersecurity, addressing legacy systems, real-time monitoring, and ICS threats. Our OT services seamlessly integrate with comprehensive cybersecurity solutions for enhanced protection.

Pen Testing from DeepSeas RED Starts Company’s Cyber Transformation
DeepSeas RED transforms cybersecurity with long-term partnerships, not just annual reports. Our pen testing ensures meaningful change and guides clients to a safer place.

Manufacturer Reduces Response Time to Cyber Threats by 90%
DeepSeas accelerates cybersecurity transformation, reducing response time to threats by 90% and phishing incidents by 77% within just 30 days. Experience rapid results today!
GET MEANINGFUL OUTCOMES FAST.
DeepSeas FAQs
At DeepSeas, we're committed to helping you understand everything involved in transforming your cybersecurity program. Below are initial FAQs to get you started.
BE THE FIRST TO KNOW.
Cyber Defense Insights from DeepSeas

Demystifying Vulnerability Management with DeepSeas
Think of your vulnerability management program like a funnel. When alerts come through, we have a variety of filters to apply to those alerts to assess which are the most immediate risks — the ones we need to act upon with the most haste.

How CISOs are Transforming Cybersecurity Programs in Three Phases
With a proactive plan, framework, and process, you can enjoy meaningful outcomes from transforming cybersecurity programs within 30 days. Our crew at DeepSeas has fine-tuned an approach to cybersecurity transformation outlined it in this video demonstration and guide.

Your EDR is Also Providing MDR. You’re Covered…Right?
Highly ranked MDR solutions, like DeepSeas, are dedicated service providers focused on delivering programs and outcomes. Whereas EDR vendors are software companies that prioritize repeatability and conformity. DeepSeas works collaboratively with you to drive quick and meaningful results.

How to Get Budget for Managed Detection & Response
You likely understand the value of 24x7 persistent defense. But what should you do if you’re struggling to get budget for MDR (Managed Detection & Response)? Below, we provide the justification you need to transform your cybersecurity program with DeepSeas MDR+ while optimizing spend.

DeepSeas Monthly Cyber Threat Intel Rollup – October 2024
Stay ahead of cyber threats with the DeepSeas Monthly Cyber Threat Intel Rollup.

Now’s the Time to Evaluate Your SIEM. Here’s How to Do It.
Whether you're considering a new SIEM vendor, optimizing your current deployment, or preparing for a complete SIEM overhaul, this guide will walk you through the essential questions and actions to perform as you evaluate your SIEM.
Using AI in Cybersecurity: How DeepSeas Leverages AI
Nate Hausrath, VP of Engineering at DeepSeas, dives into how DeepSeas leverages AI to provide persistent defense to clients.

DeepSeas Monthly Cyber Threat Intel Rollup – September 2024
Stay ahead of cyber threats with DeepSeas' Monthly Cyber Threat Intel Rollup.

The DeepSeas AI Security Model
Building an AI risk management program involves a multi-layered approach that starts with strategy and governance before moving on to technical solutions. The first step is to develop a risk strategy that includes understanding data classification, assessing specific AI-related risks, and adopting acceptable use policies.

Vulnerability Assessment vs. Penetration Test
There are key differences between a vulnerability assessment and penetration testing. Does your team use these terms interchangeably?

DeepSeas Monthly Cyber Threat Intel Rollup – August 2024
Stay ahead of cyber threats with DeepSeas' Monthly Cyber Threat Intel Rollup.
Join our Team
21% of the DeepSeas crew are Veterans or Active Military Reservists. Join our talented crew of cyber experts.